December 17, 2025
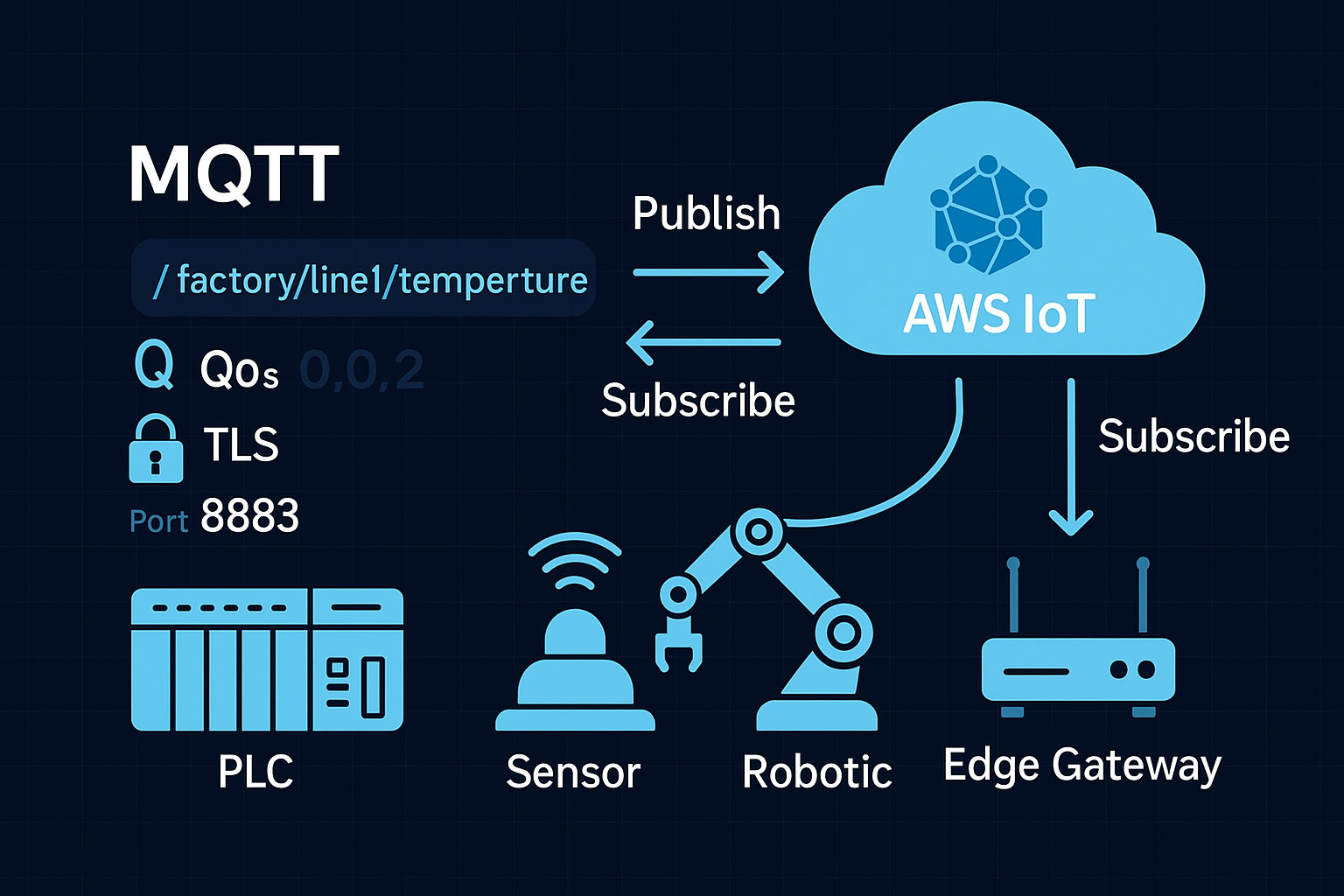
Collecting data from legacy industrial equipment and sending it to cloud platforms is a common requirement in modern manufacturing facilities. This tutorial explains how to connect industrial devices like PLCs (Programmable Logic Controllers) to AWS IoT Core using the MQTT messaging protocol.
This guide covers the complete process from device registration to data transmission, using a practical example of reading sensor data from a Modbus TCP device and publishing it to AWS IoT.
Equipment and Setup Overview
For this implementation, you need three main components:
Industrial Device: A PLC or industrial controller with Modbus TCP communication capability. In this example, we use a controller with an analog input module connected to a potentiometer.
Industrial IoT Gateway: An edge device that bridges the industrial controller and the cloud platform. This gateway runs Node-RED software for data collection and protocol translation.
AWS IoT Core: The cloud-based MQTT broker that receives and processes the industrial data.
The data flow works as follows: the IoT gateway collects data from the industrial controller using Modbus TCP protocol, then acts as an MQTT client to publish that data to the AWS MQTT broker.
Registering Your Device in AWS IoT Core
Before sending data to AWS IoT, you must register your device in the AWS IoT console. This registration establishes the device identity and enables secure communication.
Log into your AWS IoT console and navigate to the Manage section. Under Things, select "Register a thing" and choose "Create a single thing." Provide a meaningful name for your device—for example, "demo_device" or something that identifies the equipment or location.
After entering the device name, proceed to the certificate creation step. This is where AWS generates the security credentials needed for authentication.
Creating and Downloading Security Certificates
AWS IoT uses X.509 certificates to authenticate devices connecting to the platform. When you click "Create certificate," AWS generates several files you need to download:
- Device certificate
- Private key file
- Public key file
- Root CA certificate
Download the first three certificates directly to your computer. The root CA certificate requires an additional step—clicking the download link opens a separate webpage displaying certificate options.
Select the first root CA option (Amazon Root CA 1), which opens another page showing the certificate text. Copy this entire text block and save it to a file named "AmazonRootCA1.pem" on your computer. Store this file in the same folder as your other downloaded certificates.
After downloading all certificates, activate them in the AWS console by clicking the "Activate" button. This step enables the certificates for authentication.
Complete the device registration process by clicking through the remaining screens. Your device is now registered with AWS IoT Core.
Configuring Authorization Policies
Authentication verifies device identity, but authorization determines what actions the device can perform. AWS IoT uses policies to define these permissions.
From the AWS IoT console homepage, navigate to Secure, then select Policies. Click "Create a policy" and provide a policy name such as "iot_policy."
The policy defines three key elements:
Actions: What operations the device can perform (publish, subscribe, receive, connect)
Resources: Which topics or resources the device can access
Effect: Whether to allow or deny the specified actions
For testing purposes, you can use wildcards to grant broad permissions. Set the Action field to an asterisk () to allow all operations including publish, subscribe, and connect. Set the Resource field to an asterisk () to permit access to all topics.
After creating the policy, you must attach it to your device. Navigate to Manage > Things, select your registered device, click Security, and choose the certificate you created earlier. Under Actions, select "Attach policy" and choose the policy you just created.
Your device now has both authentication credentials and authorization permissions to communicate with AWS IoT.
Getting Your MQTT Broker Endpoint
To publish data to AWS IoT, your gateway needs the MQTT broker address. Find this on your AWS IoT console homepage by selecting your device and clicking the "Interact" tab.
The REST API endpoint shown here is your MQTT broker address. It looks something like: xxxxxxxx.iot.region.amazonaws.com. Copy this address—you'll need it for the Node-RED configuration.
Configuring Node-RED on the IoT Gateway
Node-RED provides a visual programming interface for configuring data flows. Access the Node-RED editor by entering your IoT gateway's IP address in a web browser followed by port 1880 (for example: 192.168.1.100:1880).
Setting Up the MQTT Connection
Drag an MQTT output node onto the Node-RED canvas. Double-click to configure it and select "Add new MQTT broker." Enter the following settings:
Server: Paste your AWS REST API endpoint
Port: 8883 (the standard port for MQTT over SSL/TLS)
Client ID: Use your device name (demo_device)
Enable the SSL/TLS option and click the pencil icon to add new security configurations. Upload the four certificate files you downloaded earlier:
- Certificate file
- Private key file
- CA Certificate (AmazonRootCA1.pem)
Name this certificate configuration (for example, "AWS_certificates") and save it.
In the MQTT node settings, specify the topic you want to publish to. Using your device name as the topic (like "demo_device") makes it easy to identify data sources.
Creating the Modbus Data Collection Flow
To read data from your industrial controller, you need to create a Node-RED flow that collects Modbus data and formats it for MQTT transmission.
Add an inject node to trigger data collection at regular intervals. Configure it to repeat every 5 seconds for consistent data updates.
Add a function node to prepare the Modbus read request. This node should create a message object specifying:
- Function code (for example, 3 for holding registers)
- Unit ID (the Modbus device address)
- Register address (where your data is stored)
- Quantity (how many registers to read)
Add a Modbus client node and configure it with your industrial controller's IP address. This node sends the read request and receives the response.
Add another function node to convert the Modbus response into a usable format. For analog values, this typically involves converting raw register values to floating-point numbers representing engineering units.
Connect a debug node to verify you're receiving data correctly before publishing to AWS.
Testing Data Transmission
Deploy your Node-RED flow by clicking the Deploy button. Check the debug panel to confirm data is being read from your industrial device every 5 seconds.
Once you verify local data collection works correctly, connect your flow to the MQTT output node. This starts publishing data to AWS IoT Core.
To verify data arrives at AWS, return to your AWS IoT console and navigate to the Test section. Subscribe to your device topic (demo_device). You should see messages appearing every 5 seconds containing your sensor data along with timestamps.
Adjust your sensor input (turn the potentiometer in this example) and watch the values change in the AWS console, confirming end-to-end data flow.
Data Format and Timestamps
When Node-RED publishes messages to AWS IoT, it automatically includes timestamp information. This allows you to track when each measurement was taken, which is essential for time-series analysis and troubleshooting.
The data appears in JSON format in the AWS test console, making it easy to parse and process with AWS services like Lambda, DynamoDB, or analytics tools.
Next Steps for Industrial Data Projects
Once data flows reliably to AWS IoT Core, you can build additional functionality:
- Store historical data in databases for trend analysis
- Create dashboards to visualize equipment performance
- Set up alerts for out-of-range conditions
- Apply machine learning models for predictive maintenance
- Integrate with enterprise systems like MES or ERP
Security Considerations
This tutorial uses broad permissions (wildcards) for testing purposes. In production environments, restrict policy permissions to only the specific topics and actions each device needs. This follows the principle of least privilege and reduces security risks.
Regularly rotate certificates and monitor device activity logs to detect any unusual connection patterns or unauthorized access attempts.
Summary
Connecting industrial devices to AWS IoT requires several configuration steps: registering the device, generating security certificates, creating authorization policies, and configuring the data collection flow. Using an industrial IoT gateway with Node-RED simplifies this process by providing visual programming tools for protocol translation and data formatting.
Once configured, this architecture enables reliable data transmission from factory floor equipment to cloud platforms where you can apply analytics, create visualizations, and integrate with other business systems.



